Cyber Security
Can You Get Hacked by Opening an Email? Facts Unveiled
Every day, over 300 billion emails are sent around the world. Many of these emails hide dangers. People often wonder if just one click or a quick look can lead to hacking. Most email clients and webmail services block harmful scripts. But, the biggest danger comes from clicking on bad links or downloading strange attachments.…
Read MoreSafeguard Your Data with Differential Backup
Studies show that about half of all companies face unexpected data loss. This puts their important files at risk. A differential backup is a smart solution. It only saves the changes made after the last full backup. This method saves a lot of time and reduces storage needs. It’s a fast and efficient way to…
Read MoreFailover Plan Essentials for Business Continuity
Recent studies show that almost one in three companies face big challenges when their systems go down. This is a clear warning for any business looking to keep its profits and good name safe. A good failover plan is key when disaster hits. It makes it easy to switch to backup systems, avoiding losses in…
Read MoreSecure Your Data with Endpoint Backup Solutions.
More than half of small businesses fail within six months after losing major data. This shows how vital it is to protect important files for smooth operations. Endpoint backup solutions are key in preventing lost productivity due to device failures, accidental deletions, or cyber threats. CrashPlan and other trusted providers automatically store and version files.…
Read MoreRaid Cyber Security Solutions – Protect Your Data
At least half of serious data disruptions come from unexpected hardware issues. This shows why organizations need a strong plan to protect valuable information. Raid cyber security leads the way, using a redundant array of independant disks to keep data safe. The raid acronym computer experts use shows its power. If one disk fails, the…
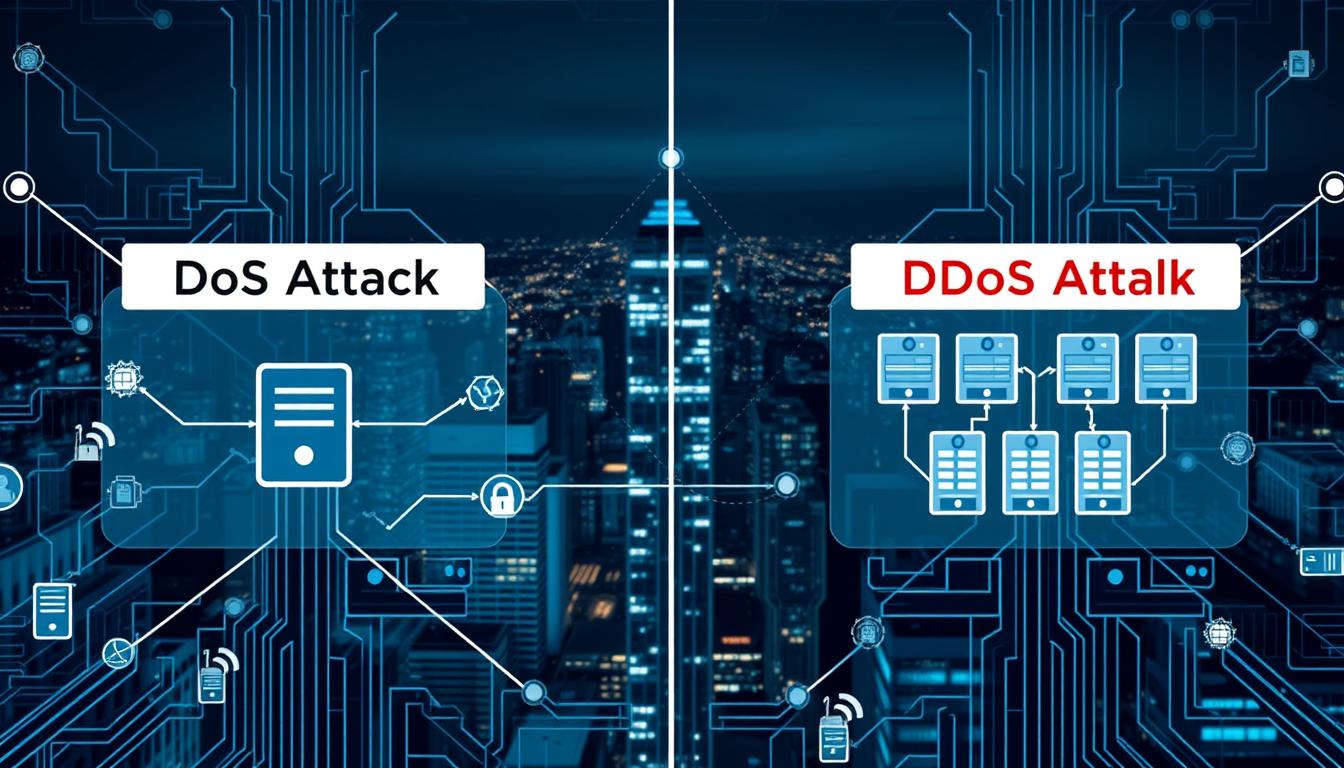
Read MoreUnderstand the Difference: DoS vs. DDoS Attacks
Every day, thousands of denial-of-service attacks hit businesses around the world. These attacks can use up a lot of resources. They can also make servers slow down or crash. This leaves users unhappy and puts important operations at risk. In a dos vs ddos scenario, a single attacker might use basic floods from one source.…
Read MoreMaximize Efficiency with IT Asset Management
Did you know that a good IT asset management plan can save up to 30% in costs? This method, called IT Asset Management (ITAM), helps track hardware, software, and infrastructure. It gives a clear view of each asset’s value and where it is, reducing surprises. A solid asset management IT system keeps teams organized and…
Read MoreEfficient RMM Agent Solutions for IT Management
N-able was voted the number one RMM Platform for three years in a row. This shows how important a good rmm agent is for better IT work. MSPs and tech teams use remote tools to watch systems, fix problems, and improve security. When people ask, “what is rmm agent?”, it’s a small but key software…
Read MoreSecure Your Home Network with Residential VPN
Did you know Mysterium VPN offers over 20,000 residential IP addresses in more than 135 countries? This shows how a residential VPN can protect every device at home. A residential ip vpn sends your traffic through real internet service provider IPs. Providers like KeepYourHomeIP and StarVPN offer dedicated or rotating IPs. This makes your online…
Read MoreUnderstanding DRM in Your Web Browser: What Is DRM in Browser?
More than 70% of streaming sites, like Netflix, use DRM to keep their content safe. This shows how key it is for browsers like Chrome or Firefox to protect against unauthorized access. Many people wonder about the digital rights management definition, which helps protect creators and keeps content safe. Digital rights management is more than…
Read More