Security
Why is 2FA so Important?
Two factor authentication, or 2FA, is a growing necessity for anyone that cares about security. It’s a relatively new addition to IT security networks, but it is one of the simplest and best ways to add an extra layer of security. 2FA is essentially as secondary login confirmation that is needed before someone can access…
Read More5 Essential IT Services You Should Get From an MSP
Outsourcing IT is becoming a more popular option than ever to help businesses that need affordable and effective IT solutions. But many businesses find that their outsourced IT does not give them the results they want. This leaves them wondering why they are paying for IT services at all. Too often businesses wait for their…
Read MoreNew Approaches to Malware Protection
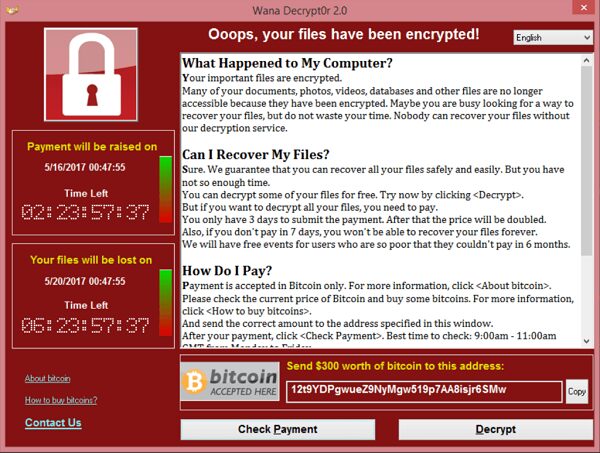
Protecting your IT system against Malware is one of the most important parts of any data management plan. These troublesome programs are always updating and finding new ways to cause trouble in people’s systems. Luckily, as the attacks have evolved so have our strategies to fight them off. Following the updates in malware protection and…
Read More‘Internet of Things’ Breach Sounds the Alarm (Literally)
Hackers usually like to work quietly, but that’s not always the case … as residents of Dallas can now attest in a recent Internet of Things breach.
Read MoreHacking the Internet of Things: What Does Your Toaster Know About You … and Who Does It Tell?
You may have heard of the Internet of Things, or seen the IoT acronym and wondered what it means… especially now that hacking may be part of the equation. The IoT refers to “smart” devices (having sensors or CPUs) that are also connected to other devices so they can share information or execute commands via…
Read MorePhishing First Aid
Your work day has just begun. You’re waiting for your coffee to cool enough to sip as your computer powers up. You open your email inbox. You see a message from your bank. You bemusedly wonder why your bank is sending a message to your work email rather than your personal address. You open the…
Read MoreWhat Information is AutoFill Giving Away?
We often address the subject of security, so we want to warn you about new trick being employed by hackers: the information AutoFill is giving away. If you’ve ever completed an online registration for anything, you’ve probably encountered the “autofill” function used by Google Chrome, Safari and other programs. This is when your computer tries to…
Read MoreAs If You Don’t Enough to Be Afraid Of… Introducing Self-coding Computer Viruses
Take just about any fictional monster, and somewhere there’s a fictional mad scientist who wants to make it even more dangerous. (Anyone remember Jurassic World?) Well, how about taking oh-so-real malware-nasty strings of code that cripple networks, steal data and generally wreak mayhem on the world … and imbuing it with artificial intelligence? Welcome to…
Read More