Adding a VPN connection to your cyber security network is always a great choice. It was one of the easiest and most inexpensive ways to help protect yourself from threats online. But what is a VPN and how does it help keep your business safe?
What is a VPN?
A VPN is a Virtual Private Network. It is essentially a private network or tunnel that connects and hides user’s IP address.
Every device has an IP address that is identified with a unique set of numbers that look something like this: 213:1.0.452.12. These numbers are used to identify that your device is trying to connect to the website’s server. So basically your IP address is taking information from the websites server so that you can connect to it. However, the website is taking your IP address and learning information from that as well. 
Your IP address is linked to your Internet Service Provider and the area of the world that users operate. This can be used to restrict content to certain regions.
For example, maybe Netflix only shows certain shows in the US that they don’t have on other countries options. They show you the content that is available based on your IP address. So if Netflix can tell that your IP address is in the US then they will restrict content to what is only allowed within the US.
So Why is This Important?
When you use a VPN you are basically connecting to a server within the virtual private network. This server can be in whatever region of the world the VPN has servers in. This allows you to hide your actual IP so the websites see the IP address of the VPN, not your actually address.
Hiding your IP is a great way to add security. Those websites are taking your IP address and using it to connect to their servers. This takes away your anonymity and people can use sneaky ways to get into your network. This is especially true when using public Wi Fi.
Public Wi Fi will always be more insecure that a private home network. Using a VPN on public Wi Fi is an easy way to help protect yourself from people who might want to attack you through a similar internet connection.
I’ve Heard of a VPN Tunnel. What is that?
Another way to think about connecting to a VPN network is that it’s creating a tunnel that transports your connection safely. Your data is encrypted and transmitted in a much safer way.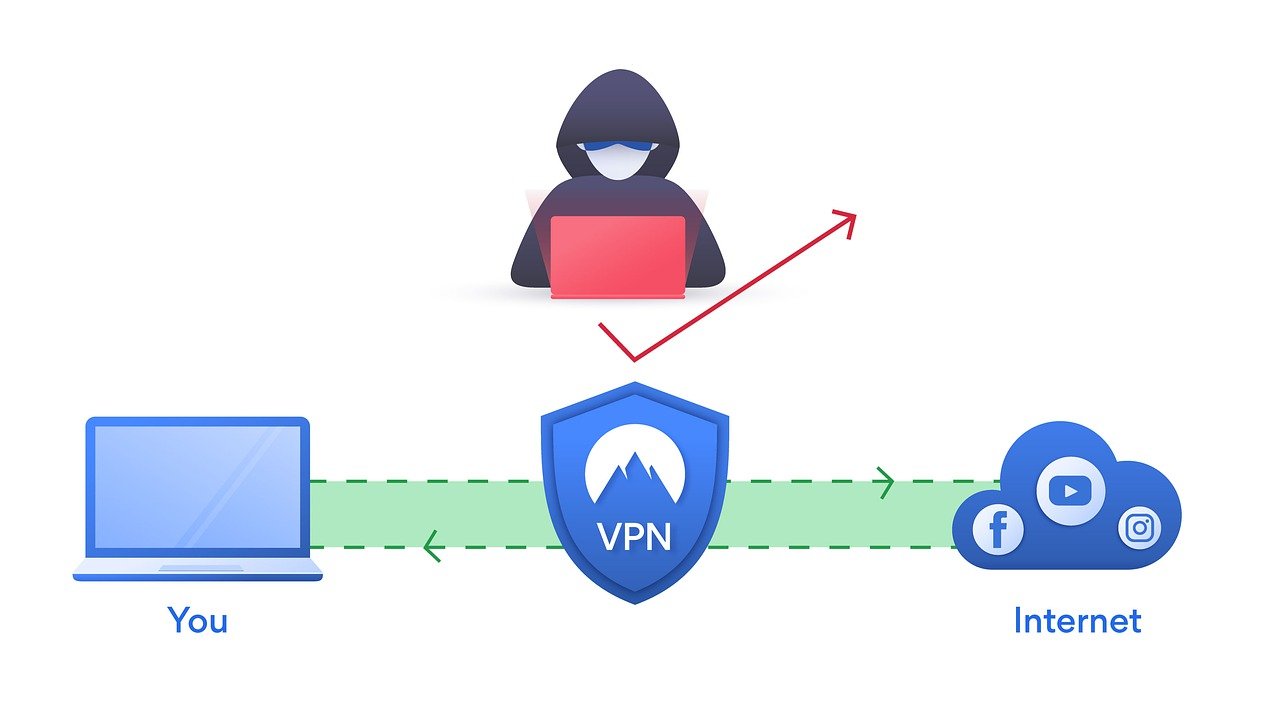
So instead of sending an unprotected connection out into the wilds of the internet, you use a VPN to help create a tunnel through all the complex data systems that safely transports you information where it needs to go.
The VPN hides your true IP so anyone who attacks this tunnel does not have access to your direct network. It helps keep you safe.
A VPN tunnel is also a great way to create safe networks for organizations to work remotely.
VPN tunnels allow users to safely transmit data to people who are on the same network. If they are not in the VPN tunnel then they will not be able to see the data. In other words, it’s protected from those outside the network.
Getting a VPN
Getting a VPN for your organization is essential if you care of security. It is a cheap, easy, and consistent way get more security in your network.
VPN providers offer different services depending on the your needs. A large company might want a dedicated VPN server so that everyone can safely connect no matter where they are.
Other smaller and personal operations might only need basic services, but that means that your VPN server might change all the time. This can be harder for people who need to communicate together safely, often.
Regardless of what VPN service you choose there is no doubt that it will help keep you safer. VPNs are essential pieces of security and should be used by everyone who cares about keeping themselves safe online.
Are Your Cybersecurity Essentials Covered?
Don't wait until a threat strikes to protect your organization from cybersecurity breaches. Download our free cybersecurity essentials checklist and take the first step toward securing your digital assets.
With up-to-date information and a strategic plan, you can rest assured that your cybersecurity essentials are covered.
Get the Checklist
Posted in:
Share this

