Read the Blog

The Time to Strengthen Your Cyber Defense is Now
The Cyber War Battlefield Has Changed The time to improve the information security structure of your business is now; such...

What You Should Know About Cyber Security Insurance
Businesses And International Cyber Warfare At the Q1 2022 Business Roundtable conference hosted by the White House, United States President...

How to Increase Smartphone Security
The state of mobile security around the world is a popular topic of conversation among SynchroNet technicians. We get to...

How Office Printers Can Be Compromised by Physical Security Hackers
Within hacking culture, certain methods to break into IT systems hold more weight than others. News about complex, daring, and...

How Cyber Security Risks Can Turn Into Physical Security Threats
The crossroads of information security and physical security is something that we closely follow at SynchroNet. Ever since manufacturers of...

The Vulnerabilities of Modern Physical Security Systems
The advent of physical security devices that connect to the Internet of Things (IoT) has been a boon for hackers...

Why Cyber Security Relies on Physical Security
We can no longer think about information security as a business process that is separate from physical security. These two...
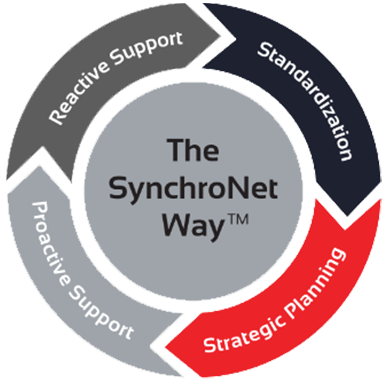
The Way
Want to move your business IT from the wild, wild West to an island of serenity? We get it, and we’ve helped transform everyday work life for hundreds of clients using The SynchroNet Way.
With our approach you get:
-
Standardization and a 100-point Best Practices checklist assigned to a dedicated network administrator.
-
Strategic planning at an executive level with a dedicated vCIO that keeps you on track for the long run.
-
Proactive support that monitors and protects your systems around the clock.
-
Reactive support from our friendly and caring customer support team who are always on the lookout for repeat issues.