Read the Blog

Fight or Flight Amid the Challenges?
The fight or flight response refers to a physiological reaction that arises in the face of something that is either...

Effectively Working From Home During Coronavirus Stay at Home Orders
Businesses around the globe have taken difficult but necessary actions to protect the health of their staff during the Coronavirus...

How Coronavirus Has Shaped Our Company
We wanted to share our own experiences so far with coronavirus and not how it has been difficult, which it...

Finding a Managed IT Support Company in Buffalo
Every company that relies on computing to do business needs help with their IT at times. It can be as...

Cloud Computing
Cloud Computing Five Things To Know About the CloudCloud computing is always changing. That is why you should stay updated...

IT Support
Any business worth their salt understands the importance of having adequate IT support. At SynchroNet, we offer just that. We...

Microsoft Office 365
Outsource IT services are quite valuable for companies that do not have an IT support department. In most cases outsourcing...
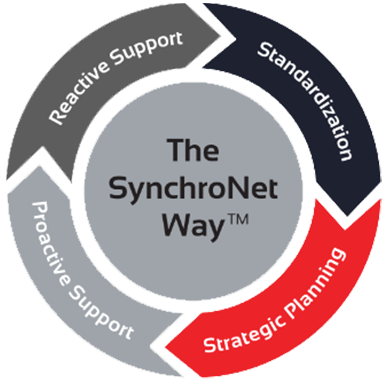
The Way
Want to move your business IT from the wild, wild West to an island of serenity? We get it, and we’ve helped transform everyday work life for hundreds of clients using The SynchroNet Way.
With our approach you get:
-
Standardization and a 100-point Best Practices checklist assigned to a dedicated network administrator.
-
Strategic planning at an executive level with a dedicated vCIO that keeps you on track for the long run.
-
Proactive support that monitors and protects your systems around the clock.
-
Reactive support from our friendly and caring customer support team who are always on the lookout for repeat issues.